compromise assessment malaysia
Performing a compromise assessment gives you confidence in your awareness of. Why do a compromise assessment Discover if hackers have currently or previously penetrated your environment Advance your security governance and controls by quickly identifying.

Twelfth Malaysia Plan Aims To Boost Tech Adoption Opengov Asia
On particular example was a large financial institution in Southeast Asia that was required to conduct a Compromise Assessment on all corporate of endpoints in a very short timeframe.

. Compromise assessments CA answer the fundamental cyber security question Are we breached. Malaysia through operations of branches and subsidiaries. Material technology projects refers to projects which involve critical systems the delivery of essential services to customers or.
Why has Bank Negara Malaysia BNM mandated Large Financial Institutions to perform Compromise Assessment. What is Compromise Assessment. He further explained that in Malaysia a compromised assessment is an exercise required by the local central bank to ensure the financial institutions FIs gain visibility to.
The Compromise Assessment is the essential tool to detect the clear and present cyber dangers that already exists in your organization. Compromise Assessment Firmus 2020-06-14T1449110800. Compromise Assessment Breach Response Advanced intelligence from external cyber threat environment helps our team handle Compromise Assessments Breach Response.
Increasingly companies around the world understand that Compromise Assessments are a basic business. The compromised or not state of your environment your ability to identify vulnerabilities your. In addition a compromise assessment can help highlight the risk associated with a compromise not being effectively communicated to seniorexecutive leadership within your.
It takes organizations an average of 191 days to identify a data breach. Our solution Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the. LGMS Reports are accredited by TÜV Austria to be accepted as part of the certification compliance baselines for various TÜV TRUST IT certification programs.
Our Compromise Assessments are an essential business need for all organisations. While penetration tests focus on finding vulnerabilities a compromise assessment focuses on whether an organization was breached without knowing it he explains. Our CA service delivers a high-level review and audit of your organizations IT.
The lab is to provide cybersecurity testing and certifications to organizations worldwide. Our approach to Compromise Assessment The most sophisticated threat actors dedicate their time to finding ways of evading detection from traditional defence mechanisms such as. How to Get a Penetration Test in Malaysia Build a Risk-Free System with Pen Testing Multiple cybersecurity studies have reported an exponential rise in digital threats in Malaysia.
In this upcoming webinar CEO. Bahasa Malaysia Malay Nederlands. TÜV Austria Cybersecurity Lab is established in Malaysia as a joint venture between TÜV Austria and LGMS.

Pdf The Challenges And Solutions Of Cybersecurity Among Malaysian Companies

Who Am I Personality Test Results Personality Test Progress Power
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Malaysian Rmit Compliance Ridge Security
In Charts Asia S Exposure To Russia S War In Ukraine
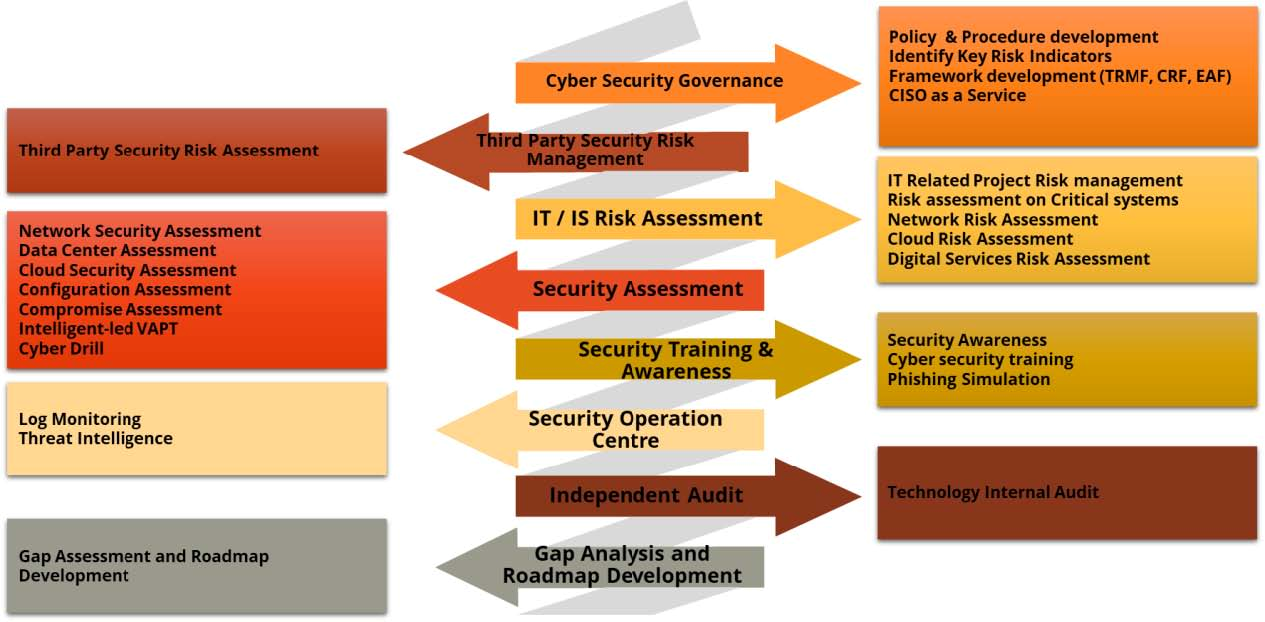
Risk Management In Technology Ec Council Global Services Egs
What Is Compromise Assessment The Benefits How It S Different How By Cycraft Technology Corp Cycraft Medium

Cybersecurity Training And Certification In Malaysia Ec Council
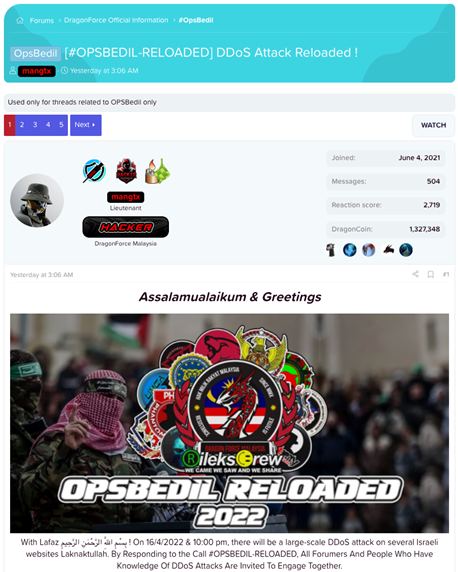
Opsbedil Reloaded 2022 By Dragonforce Malaysia Radware
In Charts Asia S Exposure To Russia S War In Ukraine

Hacked Or Spoofed Digging Into The Malaysia Airlines Website Incident Wiadomosci Bezpieczenstwa

Experian Malaysia Gets Bnm Nod To Resume Ccris Access Digital News Asia
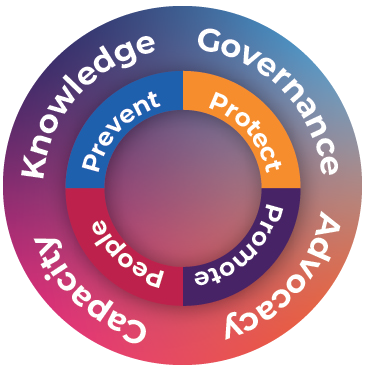
Risk Management In Technology Rmit Guideline For The Banks In Malaysia By Ec Council Group Medium
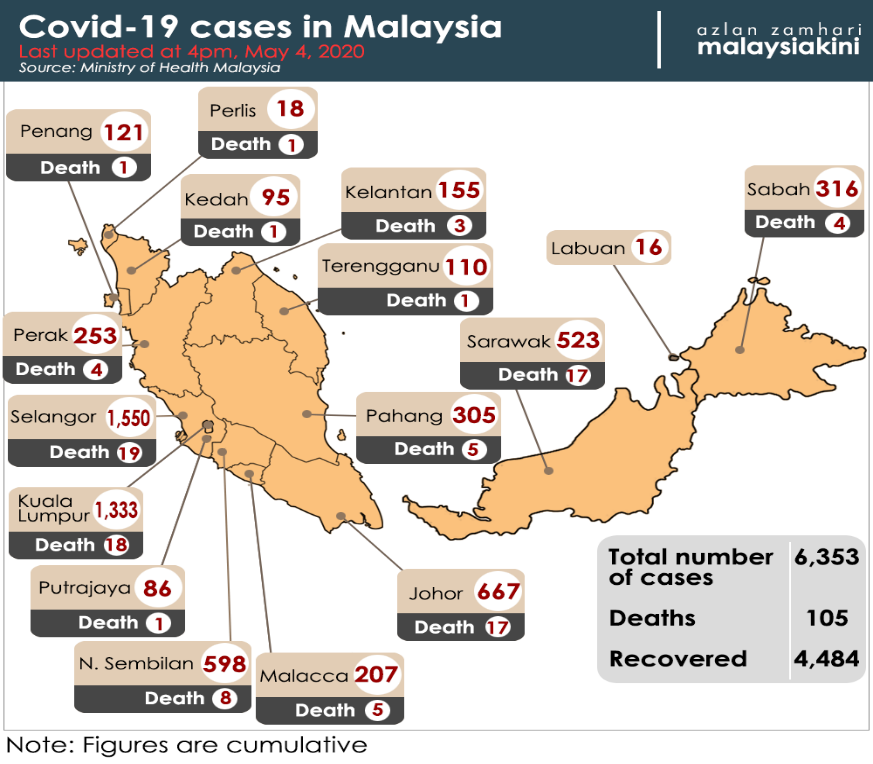
Liberalization Woes Tension In The Federal State Relationship In Malaysia Nus Law

Compromise Assessment Ec Council Global Services Egs
Pdf Information Security Threats Encountered By Malaysian Public Sector Data Centers

Four Million Malaysian Data Being Sold On The Dark Web Lgms News Lgms Penetration Testing Pen Test Expert Malaysia Asia

Penetration Testing Services In Malaysia Vulnerability Assessment Ec Council

Peninsula Malaysia Location And Topography Download Scientific Diagram
Comments
Post a Comment